_(11).png)
What are Private and Public Keys?
In the realm of encryption and secure communication, private keys and public keys play an essential role in ensuring the confidentiality, integrity, and authenticity of data. These two keys are part of a cryptographic system known as asymmetric encryption or ...
.jpg)
What is Encryption?
Encryption is the process of converting data into a coded form to prevent unauthorized access. It is used to protect sensitive information by transforming it into unreadable text using algorithms, making it accessible only to those with the correct decryption ...

What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) is an extra layer of security used to ensure that people trying to gain access to an online service are who they say they are. It requires two forms of identification before granting access: something the user ...
.jpg)
What is a Replay Attack?
A Replay Attack is a type of cyber attack where an attacker intercepts and records a legitimate communication between two parties (such as a user and a server) and then replays it to gain unauthorized access to a system. Instead ...

What is a Man-in-the-Middle (MITM) Attack?
A Man-in-the-Middle (MITM) attack is a type of cyberattack where an attacker secretly intercepts, alters, or relays communication between two parties (such as a user and a website) without their knowledge. The attacker essentially positions themselves between the two communicating ...
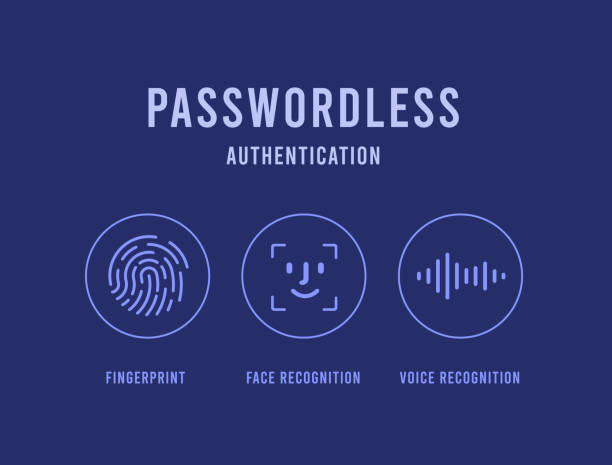
What is Passwordless Authentication?
Passwordless authentication is a modern security method that allows users to authenticate without the need for a traditional password. Instead of relying on something the user knows (like a password), this approach leverages something the user has (such as a ...